Cyber Market Update March 2022
By Newfront | Published March 21, 2022

Due to increased tensions and sanctions placed on Russia, the United States government has issued a warning that retaliatory cyberattacks may increase. All organizations need to be vigilant by having a plan in place in case of a cyberattack.
There is a heightened focus on the war exclusion in cyber policies and how it may be applied to potential cyber attacks related to the conflict between Russia and Ukraine. War exclusions are part of many types of insurance policies, including cyber. The applicability of the exclusion depends on policy language and facts of the claim. Unfortunately, there is no standardization of war exclusion wording or cyberterrorism definitions amongst policies. War exclusions for cyberattacks have been under scrutiny following the court ruling over losses stemming from the 2017 NotPetya malware attack. The risk of cyberattacks with wide-ranging effects has increased for insurers writing cyber, and other coverages including property, cargo, aviation, trade credit and political risk.
Organizations should prepare themselves, ensuring their cyber defenses are as strong as possible, and their incident response plans can be quickly implemented if an attack occurs.
Underwriting Trends
The Cyber market remains hard as ransomware events have elevated losses. Cyber carriers continue to increase premiums and require strong cyber hygiene for Insureds. Renewal trends and minimum security requirements remain as previously reported in December 2021.
The cyber marketplace has also been impacted by the increasing supply chain risk. The SolarWinds breach highlighted how a breach at one company can have a much larger impact across the economy. Insured losses are reported to be $90M+.
The Log4j software vulnerability came to light in December 2021, and was deemed the most serious vulnerability seen to date by cybersecurity officials. One of the most concerning issues is Log4j’s position in the software ecosystem, and its widespread use. It is used in cloud services like Apple iCloud and Amazon Web Services, as well as a wide range of programs from software development tools to security tools. It is hard to know if Log4j is being used in any given software system because it is often bundled as part of other software. Fixes require different approaches, including patching, updating to a new version of software, wholesale system update, or removing vulnerable code manually.
Carriers have added questionnaires at renewal regarding use of SolarWinds software, Microsoft Exchange, Log4j logging utility, and risk mitigation efforts to underwrite the risk. They are also scanning for vulnerabilities as part of the underwriting process. As the risk from vendors remains high, we are also seeing reduced limits for Contingent Business Income limits from most carriers.
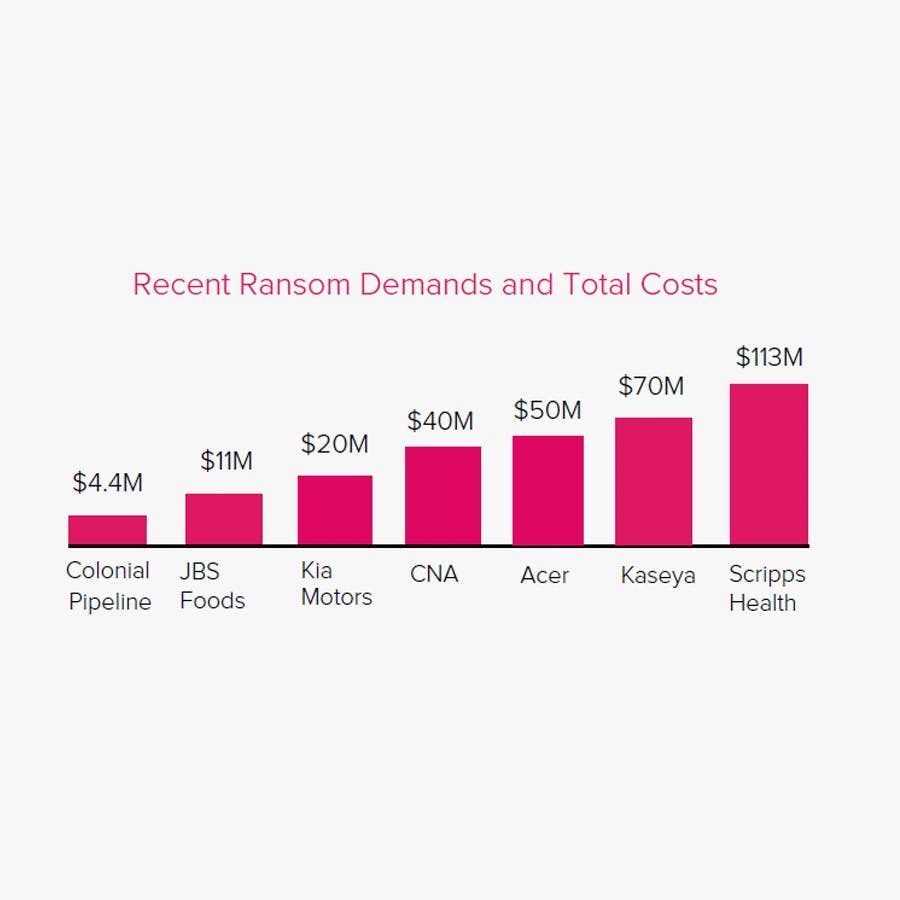
Recent Ransom Demands and Total Costs
All industries are at risk. Technology, food production, financial services, healthcare, and critical infrastructure firms were hit with nearly $310 million of ransom demands in 2021.
Renewal Process
Start early allowing the underwriting process as much time as possible.
Provide complete applications 45-60 days in advance. Carriers require their own forms to be completed, so anticipate there may be various forms and follow up questions.
Participate in underwriting meetings as needed, including discussions with the CISO or the Head of IT.
Complete all subjectivities prior to binding.
Premium/Capacity Trends
The cyber market is hardening fast with rates increasing 100%+ in most cases.
Larger companies with revenues $1B+ are experiencing rate increases 200%+.
Full MFA is required. Without full MFA across the enterprise, clients risk non-renewal or significant rate increases, retention hikes, coinsurance, or reduced coverage.
Primary limits are being reduced and key coverages such as Cyber Extortion/Ransomware, Cyber Crime, Contingent Business Income, Hardware Replacement, are being sublimited.
Policy layers of $10M limits, which were typical in the past, are being reduced to $5M making the need to have twice as many carriers on a program to secure the same total limits. In some instances, maintaining expiring limits may not be possible.
Given the increasing severity of losses, excess insurers may seek higher rate increases on a percentage basis than the primary layer.
Key Cyber Security Minimum Requirements
Full multi-factor authentication (MFA) across the enterprise is required- email, remote access, and privileged users.
Endpoint protection (EPP) and endpoint data and response (EDR) protection.
Plan for end-of-life or end-of-support products replacement. Products still in use must be kept segregated from the network.
Backup data must be kept separate from your network (offline) or in cloud designed for this purpose.
Frequent security awareness training for employees. In some instances, maintaining the expiring limits will not be possible.
Business Continuity Plan with recovery time objectives.
Disaster Recovery Plan.
Cyber Incident Response Plan.
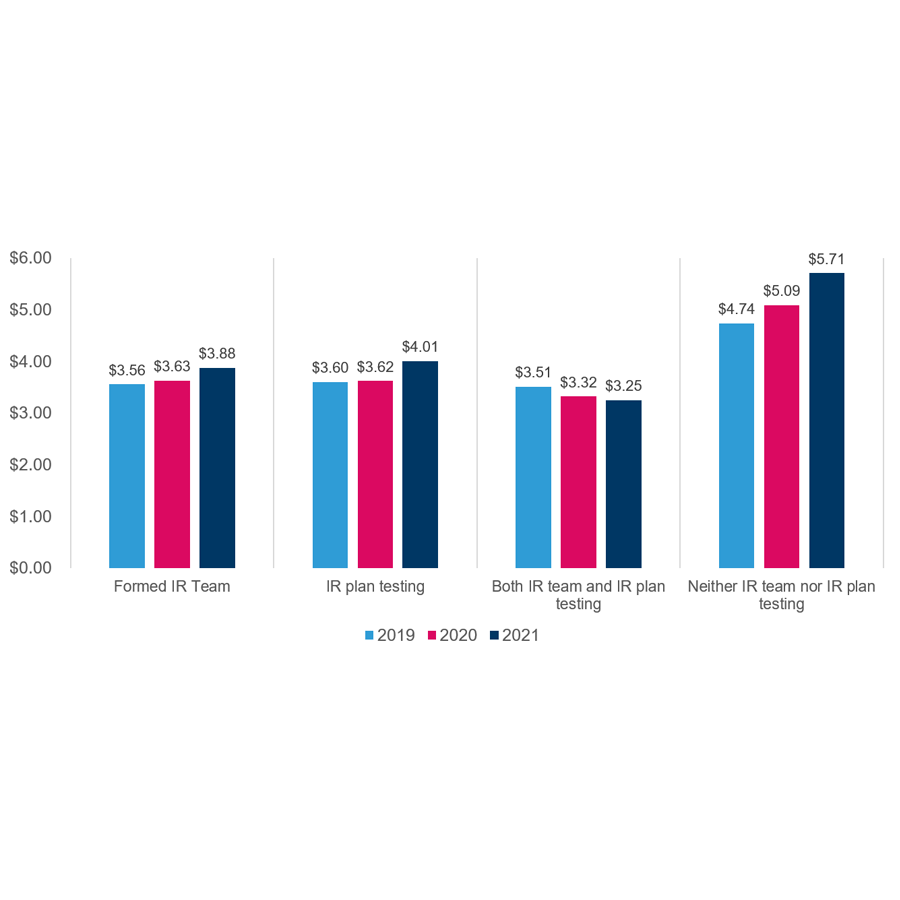
Average total cost of a data breach with incident responses (IR) team and IR plan testing
There is good news for companies that have deployed both incident response teams and incident response testing - it is the ONLY category with the average total cost of data breach trending down.

Newfront
Newfront is a modern brokerage transforming the risk management, business insurance, total rewards, and retirement services space through the combination of elite expertise and cutting-edge technology. Specializing in more than 20 industries and headquartered in San Francisco, Newfront has offices nationwide and is home to more than 800 employees serving organizations across the United States and globally.